Protect Your Charlotte Business: The Complete Multi-Factor Authentication Implementation Guide
Cybercriminals are targeteting small businesses more aggressively than ever before. Recent cybersecurity reports reveal that 43% of all cyberattacks specifically target small businesses, making local companies prime targets for data breaches and financial theft.
AltrueTECH helps Charlotte businesses implement Multi-Factor Authentication (MFA) to create an unbreachable security barrier that stops hackers cold—even when they steal your passwords. This comprehensive guide shows you exactly how to protect your business with professional MFA implementation.
Why Small Businesses Need Multi-Factor Authentication Now
The business community faces escalating cyber threats daily. Small businesses often believe their size makes them invisible to hackers, but this dangerous misconception leaves them vulnerable to devastating attacks.
Cybercriminals specifically target small businesses because they typically maintain weaker security defenses while storing valuable customer data, financial information, and business secrets. One compromised password can destroy years of hard work, damage your reputation, and cost thousands in recovery expenses.
Multi-Factor Authentication transforms your business into a fortress. MFA requires attackers to overcome multiple security barriers before accessing your systems. Even if hackers steal your password through phishing emails or data breaches, they cannot penetrate your MFA-protected accounts without additional verification factors.
The FBI’s Internet Crime Complaint Center reports that businesses lose billions annually to cybercrime. Companies cannot afford to delay implementing robust security measures like MFA.
Understanding Multi-Factor Authentication: Your Digital Security Foundation
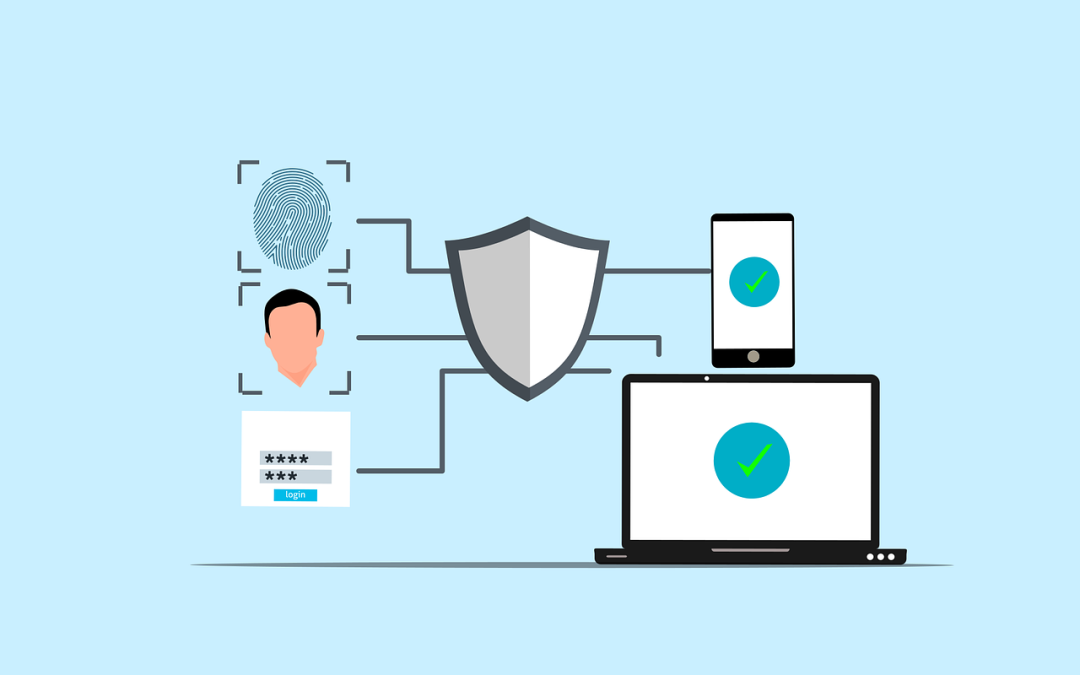
Multi-Factor Authentication requires users to provide two or more distinct verification methods when accessing business accounts and systems. This layered security approach creates multiple checkpoints that stop unauthorized access attempts.
AltrueTECH implements MFA using three core security factors:
Knowledge Factors: Something You Know
Your first security layer includes traditional passwords, PINs, or security questions. While familiar and convenient, knowledge factors alone cannot protect modern businesses from sophisticated cyber attacks. Password-only security fails against common threats like credential stuffing and brute force attacks.
Examples:
- Account passwords
- PIN numbers
- Security question answers
Possession Factors: Something You Have
Your second security layer involves physical devices or digital tokens that generate unique, time-sensitive codes. Attackers cannot access these possession factors without physically stealing your devices or compromising your secure applications.
Examples:
- SMS verification codes sent to your mobile phone
- Authentication apps like Google Authenticator or Microsoft Authenticator
- Hardware security keys from YubiKey or similar providers
- Smart cards with embedded security chips
Inherence Factors: Something You Are
Your third security layer leverages unique biological characteristics that cannot be replicated or stolen. Biometric authentication provides the strongest security factor because it identifies you personally.
Examples:
- Fingerprint scanning (common on smartphones and laptops)
- Facial recognition technology (Apple Face ID, Windows Hello)
- Voice recognition systems
- Retinal or iris scanning for high-security applications
AltrueTECH’s Professional MFA Implementation Process for Charlotte Businesses
AltrueTECH streamlines MFA implementation for Charlotte small businesses through our proven, step-by-step process that minimizes disruption while maximizing security.
Step 1: Comprehensive Security Assessment
We begin every MFA project with a thorough evaluation of your current security infrastructure. Our technicians identify vulnerabilities and prioritize systems requiring immediate MFA protection.
Critical systems we secure first:
- Email platforms (Microsoft 365, Google Workspace)
- Cloud storage services (OneDrive, Google Drive, Dropbox)
- Banking and financial accounts
- Customer relationship management (CRM) systems
- Remote desktop and VPN connections
- Accounting software (QuickBooks, Xero)
Step 2: MFA Solution Selection and Customization
AltrueTECH recommends enterprise-grade MFA solutions tailored to your specific business needs, budget, and technical requirements.
Recommended MFA Solutions:
Microsoft Authenticator: Seamlessly integrates with Microsoft 365 environments common in businesses. Provides push notifications, time-based codes, and passwordless authentication options.
Google Authenticator: Free, reliable solution perfect for small businesses using Google Workspace. Generates secure time-based codes without requiring internet connectivity.
Duo Security by Cisco: Enterprise-grade platform offering flexible authentication methods, detailed reporting, and easy integration with existing business applications.
Okta Verify: Comprehensive identity management solution that scales with growing businesses. Includes advanced features like adaptive authentication and single sign-on (SSO).
Authy by Twilio: Cloud-synchronized authenticator that allows secure backup and multi-device access, reducing user frustration when devices are lost or replaced.
Step 3: Systematic MFA Deployment
Our technicians implement MFA across your critical business systems using a phased approach that prevents operational disruptions.
Phase 1: Core Applications We secure your most sensitive systems first, including email, financial accounts, and customer databases.
Phase 2: User Account Configuration We configure MFA for all employee accounts, ensuring consistent security across your organization.
Phase 3: Remote Access Protection We implement MFA for VPNs, remote desktop connections, and cloud-based applications used by remote workers.
Step 4: Employee Training and Support
AltrueTECH provides comprehensive training to ensure your Charlotte team embraces MFA adoption. We create user-friendly guides, conduct hands-on training sessions, and offer ongoing support to address questions and concerns.
Our training covers:
- MFA setup procedures for each platform
- Best practices for managing authentication devices
- Troubleshooting common issues
- Security awareness and threat recognition
Step 5: Ongoing Monitoring and Optimization
Cybersecurity requires continuous attention. AltrueTECH provides ongoing MFA management services to keep your business protected against evolving threats.
Our monitoring services include:
- Regular security assessments and updates
- MFA effectiveness testing and optimization
- Employee access reviews and adjustments
- Incident response and recovery support
- Technology upgrades and modernization
Overcoming Common MFA Implementation Challenges
Businesses often face similar obstacles when implementing MFA. Here are some ways to avoid these common pitfalls:
Employee Resistance and Adoption Issues
Some team members may initially resist MFA due to perceived inconvenience. We address this challenge through clear communication about security benefits, comprehensive training, and selecting user-friendly authentication methods that integrate seamlessly into daily workflows.
Legacy System Integration
Older business applications may lack native MFA support. AltrueTECH evaluates your existing software and recommends integration solutions or upgrades that maintain functionality while adding security layers.
Budget Constraints
Small businesses often worry about MFA implementation costs. We help you start with cost-effective solutions like free authenticator apps, then scale to more advanced options as your business grows and budget allows.
Device Management and Recovery
Lost or stolen authentication devices can create access problems. AltrueTECH establishes device management policies, backup authentication methods, and quick recovery procedures that restore access without compromising security.
The Business Case for MFA: Protecting Your Investment
Implementing MFA delivers immediate and long-term benefits that far exceed the initial investment:
Financial Protection: The average small business data breach costs $3.31 million, according to IBM’s Cost of a Data Breach Report. MFA prevents most breaches for a fraction of that cost.
Regulatory Compliance: Many industries require MFA to meet compliance standards. Implementing MFA helps Charlotte businesses satisfy regulations like HIPAA, PCI DSS, and SOX.
Customer Trust: Customers increasingly expect businesses to protect their personal information. Visible security measures like MFA demonstrate your commitment to data protection.
Competitive Advantage: Security-conscious customers often choose businesses that prioritize cybersecurity. MFA implementation can become a differentiating factor in competitive marketplaces.
Insurance Benefits: Many cyber liability insurance policies offer premium discounts for businesses that implement MFA and other security best practices.
Why Choose AltrueTECH for MFA Implementation in Charlotte?
AltrueTECH combines deep cybersecurity expertise with local Charlotte market knowledge to deliver MFA solutions that protect your business without disrupting operations.
Our advantages:
- Local Expertise: We understand Charlotte’s business environment and specific security challenges
- Comprehensive Service: From assessment through ongoing support, we handle every aspect of MFA implementation
- Proven Results: Our Charlotte clients report significant security improvements and zero MFA-related breaches
- Scalable Solutions: We design MFA systems that grow with your business
- Rapid Response: Local support means faster issue resolution and emergency assistance
Take Action: Secure Your Charlotte Business Today
Cybercriminals continue targeting Charlotte small businesses with increasingly sophisticated attacks. Every day you delay MFA implementation increases your vulnerability to devastating security breaches.
AltrueTECH makes MFA implementation simple, affordable, and effective. Our team provides the expertise and support you need to transform your business security posture and protect your valuable assets.
Ready to protect your business? Contact AltrueTECH at 803-766-3400 or book an appointment today for a security assessment and customized MFA implementation proposal.